 2683 Views
2683 Views
Can you imagine that there will be close to 55.7 billion connected devices by 2025, 75% of which will be based on IoT platform, as per a report by IDC?
Be it remotely controlled home appliances or wearable connected fashion accessories, networked vehicle telematics sensors or connected sensor networks, all run on IoT – Internet of Things
While we revel at this new marvel, we tend to overlook the risks it comes with. Imagine a remote attacker turning the air conditioner ON in your house in peak winter or making your coffee machine overheat, thus causing an electrical fire. If that doesn’t sound scary enough, what if your vehicle suddenly accelerates and steering wheel locks up in heavy traffic?
In the context of industry, a survey conducted by Dimensions Research indicates that that 99% of IT teams report security challenges with IoT and IIoT.
Read on to know the security aspects you should take care of if you are going the IoT way.
Internet of Things and Security
Security is like a chain that is only as strong as the weakest link. Attackers can exploit vulnerability from one or more of following fronts – Network, Application, Device or Chip. In general, attackers are motivated by following factors, theft, espionage, spamming, control, disruption or simply fun.
To secure an IOT device, effectively, we need to secure all the following aspects –
-
Device Authentication – Confirming the true and unique identity of communicating devices on a network
-
Secure Communication – Protecting data in motion by maintaining the confidentiality and integrity of connections between peers
-
Secure Code Execution – Protecting data in use by ensuring the device(host) runs the software in the way it was intended at original boot and after secure updates without information leakage
-
Secure Storage – Protecting data at rest by encrypting the data and by storing it in a secure location
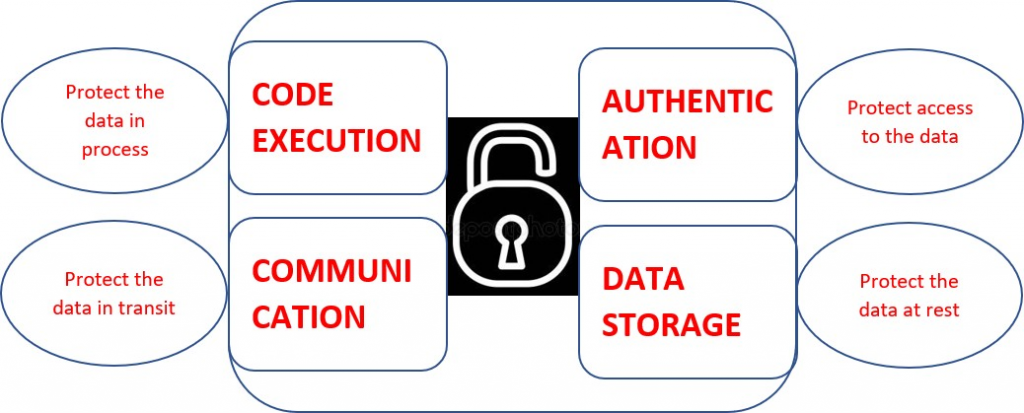
Security best practices that should be considered for an IOT infrastructure to ensure overall security
-
Understand the Risk: Huge number of IOT devices connected through heterogeneous infrastructure increases the risks of attacks which includes
- Safety: Serious injury or death occurs if an attacker successfully exploits IoT security weaknesses for example in connected cars and wearable medical devices. on a large scale, cyber terrorists could shut down an electrical grid or disable a city’s water
- Privacy: With IOT, the potential for theft extends well beyond health and financial information. For example, an attacker can breach a home video surveillance system to spy on someone or monitor smart meter data to know when someone is home.
- Theft:Remote keyless entry systems can be compromised to gain entry into homes and vehicles and smart meters could be hacked to steal
- Productivity: Highly automated manufacturing production lines can be shut down and offices can be made unstable.
-
Never under estimate your enemy – Today’s cyber criminals aren’t all stereotypical basement hackers seeking a cheap thrill and a little notoriety. they are highly motivated by factors like, financial gain terrorism, political sponsorship, etc. increasing numbers of hackers are backed by criminal organisations or rouge nations with significant financial and computing resources to carry out their attacks in a stealth mode for a prolonged
-
Minimize the attack surface – When designing a new IOT device, it may be tempting to load it up with bells and whistles. while such a design logic might be appreciated by sales team, its feared by security team for obvious reasons.it doesn’t mean that product design shouldn’t have jazzy stuff, but care should be taken to secure it from cyber-attacks.
-
Implement right security at right time – Appropriate security should be installed at the right component layer – system, board or chip, based on the environment where the system will be operating and type of attacks it can expect.
-
Authenticate connected devices – All connected devices in an IOT infrastructure must be uniquely identified and able to verify the identity and authenticity of every other communicating device in the IOTinfrastructure
-
Use standard based protocols and algorithms – Standards help to ensure interoperability and promote cooperationthroughout the IOT if a flaw or vulnerability is discovered in a standard protocol the entire community works together to fix the issue and improve the entire standard. Rather than reinventing the wheel, use of proven use of standards-based solution is a wise decision.
-
Protectdata in motion – All communications in an IOT system should be encrypted from end to end to ensure the confidentiality and integrity of data in
-
Protect data in use – Application code in an IOT system can be protected in the following ways, software mechanisms, secure element chips, and/or hardware IP
-
Protect data at rest – Considering the huge amounts of data collected by an IOT system, not only the encryption keys and unique devices identifiers, but also the storage mechanism should be well
-
Choose the right vendor – To protect your IOT system make sure you engage a trusted partner throughout your value chain who is equally committed to security and integrity of your
Conclusion
With IIoT (Industrial Internet of Things), organizations have literally struck gold by getting access to humongous valuable data, indicating that it is here to stay. While it has created opportunities beyond imagination for business, we have seen how IOT also creates many new and potentially more harmful, even lethal security threats that must be proactively and continuously addressed at every step in the product life cycle and value chain. We need to protect our customer’s sensitive data and well-being of their operators from attacks of theft, privacy, safety or productivity.
Most IOT service / solutions providers agree that security is a top concern, however, there are very few who actually have the expertise with cybersecurity protocols necessary to secure devices. As a result, many IOT devices are deployed without even a cybersecurity baseline, creating system vulnerabilities for hackers to exploit. Cyfuture’s end- to-end IOT development services and customized IOT solutions are focused on creating smart & secure environments across various sectors. For further queries and consultation, please get in touch with us on www.cyfuture.com or email us on [email protected]. Our team of subject matter experts will assist you achieve your targets in the most customised and optimal manner. We are looking forward to working with you.
Related Posts in This Category

