-
Get Cloud GPU Server - Register Now!
Toggle navigation

Data security is one of the fastest-growing priorities of companies in most industries today. This is because data breaches and cyber threats are rising exponentially, so businesses should fortify their defenses, especially on Business Process Services. If you happen to be a decision-maker or even an influential stakeholder in your organization, understanding the nuances of data security in BPS is vital. But why does it matter?
Just think of your business as a fortress. Business Process Services as the walls, the assets you manage, and the customers you serve. What if an invader finds a crack on one of the walls, though? Then, those consequences get out of control: sensitive information loss, damage to reputation, and financial implications. Consequently, you must have very robust data security measures in order to protect your fortress.
In this blog, we’ll discuss some of the essential data security features of Business Process Services and how cloud security services could be a determinant factor in protecting your business.
Now, let’s dive into the essential strategies and best practices you need to implement to ensure your data remains secure and your operations thrive.
Business Process Services are outsourced services that allow a firm to simplify its operations, enhance efficiency, and respond quickly to customers and markets. Some of the services fall under customer support, finance and accounting, human resources, and IT services, for which many other services may be provided. This has increased the data that many organizations handle by outsourcing business process services, thereby requiring greater protection of such sensitive information.
Companies deal with lots of confidential information every day-which may include customer information, financial documents, and more. When dealing with BPS, this information is usually out of the private networks and so exposed to unauthorized access and theft. Strong data security controls ensure that such information is protected from unauthorized use and stealing.
Every industry has strict regulations about data protection, such as GDPR in Europe and HIPAA in the healthcare sector. Non-compliance with such regulations may result in heavy fines and legal battles. Data security in BPS ensures the resolution of such regulatory compliance issues.
Trust is one basic building block in any successful business association. Customers need assurance that the data they provide would be treated with care and kept secure. It helps retain existing customers while also attracting new clients, fostering loyalty and long-term relationships.
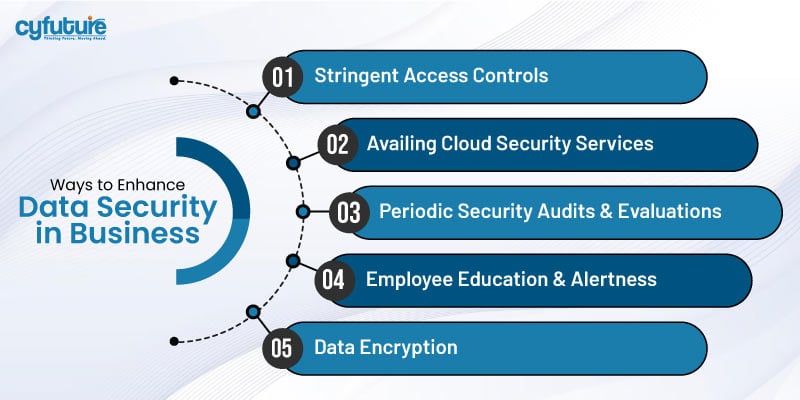
Access controls are the first major safeguard against unauthorized access of data. Access controls are stringent, such that only authorized staff members have access to even the most sensitive information. This can be through:
Role-based access control (RBAC): That is, access is granted according to a worker’s role in the organization.
Multi-factor authentication (MFA): In this case, two-factor or more authentication methods are in place instead of just passwords.
With the upsurge rate of dependency on cloud servers, integrating cloud security services is also necessary. The services protect the information stored in the cloud through strong security capabilities such as encryption, intrusion detection systems, and periodic security audits. In this aspect, organizations can minimize some risks associated with the use of cloud storage.
Data encryption is part of data security. If the sensitive data is encrypted, then it makes sure that in case the improper party gets hold of such data, it will remain unreadable without decryption. Organizations must encrypt both the rest and in-motion data: at rest, refer to stored data, and in motion, refer to data in transit.
Business organizations must carry out security audits from time to time to identify the vulnerabilities of data security protocols. Companies can remain on top of these threats by assessing current practices, pinpointing where adjustments need to be made, and staying in front of the threats while improvements are made to evolving security measures.
Staff is normally the weakest link when it comes to security. Periodical training sessions will teach the staff the importance of data security, how to identify phishing attack attempts, and how to follow best practices for safeguarding sensitive information. An informed workforce is a big asset in maintaining data security.
Selection of an appropriate data center service provider will be very suitable to ensure the data security. A good provider must possess the following features:
Redundant Systems: Assuring availability in the event of hardware failure.
Physical Security Measures: It includes implementation of access controls as well as surveillance and environmental controls in the protection of physical data storage.
Data centers are a critical aspect of Business Process Services. Outsourcing involves the trusteeship of data centers, wherein the processes are given to the data centers for storage. Here are a few key points regarding data centers.
These modern data centers use strict physical security, including closed-circuit surveillance systems, biometric access controls, and even monitoring throughout the day and night, to lock out unauthorized people from accessing sensitive data.
Data centers are equipped with advanced climate control mechanisms that prevent servers from overheating or suffering from other environmental conditions that may compromise the integrity of the data.
A good provider will have backup and disaster recovery so the data can always be recovered in a relatively short amount of time in case of an incident.
Most data center services are compliant with international standards such as ISO 27001 and SSAE 18, which can further endorse the best practices for the security of the data.
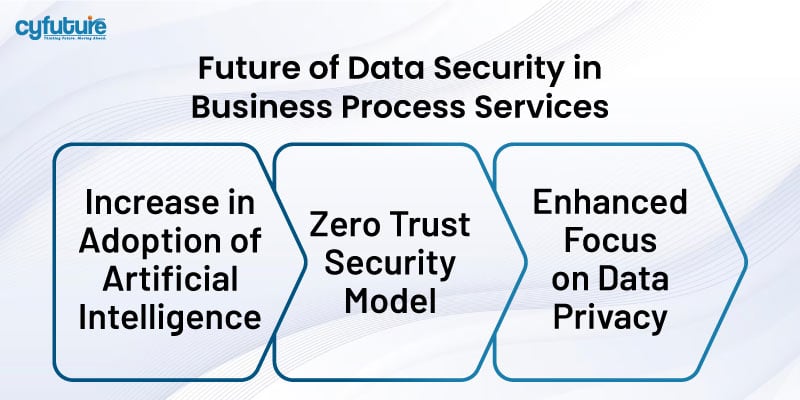
With the advancements in technology, there is bound to be a change in the data security landscape for Business Process Services. Some of the trends to expect are:
AI-powered security solutions have now become the trend in data security. These tools can process voluminous amounts of data and identify anomalies and potential risks in real time. This way, any security incidents can be responded to quickly.
This new model is the Zero Trust model, where organizations take the concept of perimeter-based security behind them and move with stringent authentication for every user and device attempting access to resources at any place. A zero trust model also ensures that even the internal users are always under surveillance.
This brings about heightened awareness regarding data privacy and therefore makes businesses realize that data handling has to be transparent. Meaningfully, its usage by companies has to be communicated to the customers and likewise, data protection requirements have also to be implemented.
Data security in Business Process Services is not only an IT issue but a business mandate. Robust security would protect sensitive information, ensure compliance with regulations, and help hold onto customers. Though technology changes continuously, being informed and proactive about best data security practices will be essential in protecting your business’s future.
This investment in proper data security measures directly translates to the success of your business. It could be through cloud security services, sure and strong data center services, or even the culture of a secure consciousness among all the employees involved. Stop waiting for the break to happen. Take action today, make your fortress stronger, and let your data not become one of the many victims of this digital age.
With the right strategies, you can ensure that your Business Process Services turn out to be a secure environment-not just in compliance but also driving growth and innovation for the business. The time for data security has come; indeed, your business warrants nothing less.