-
Get Cloud GPU Server - Register Now!
Toggle navigation

Organizations are increasingly gravitating towards cloud computing in the creation of agility and operational efficiency. However, this meteoric rise of cloud adoption raises a myriad of security concerns that are often overlooked. With businesses rushing to quickly migrate their data and applications into the cloud, they unwittingly expose themselves to a variety of possible threats. Are you overlooking these critical cloud security threats?
Cloud security is the main concern for most organizations. The huge volume of information moving between cloud service providers and organizations creates opportunities for intentional as well as accidental leaks of sensitive information from third parties to malicious ones. Moreover, cloud data breaches in numerous incidents including insider threats, human error, weak credentials, criminal activities, and malware.
Cyberthieves (state-sponsored hacking teams, for instance), want to exploit vulnerabilities in cloud services to steal information from the network of an organization they are targeting for malicious purposes. Attackers usually make use of in-built tools used by cloud services to move laterally and exfiltrate confidential data to systems that they are in control of.
Public and authentication APIs pose new security risks for cloud services. In principle, exactly what allows cloud services to be accessible by IT systems and employees makes it challenging for the organization to maintain effective control over or prevent unauthorized access to those services.
In this comprehensive blog post, we will understand the complex landscape of cloud security, key towards keeping sensitive information protected, pertinent threats organizations facing challenges in leveraging cloud computing services. Additionally, we will outline why strong Cloud Security Services in India and strategic overviews through Cloud Strategy Consulting are significant.
As we navigate through this maze of vulnerabilities, you’ll soon realize what your quintessential threats are to jeopardize your cloud environment and business continuity.
However, let’s take a look into a few stats and data before delving deep.
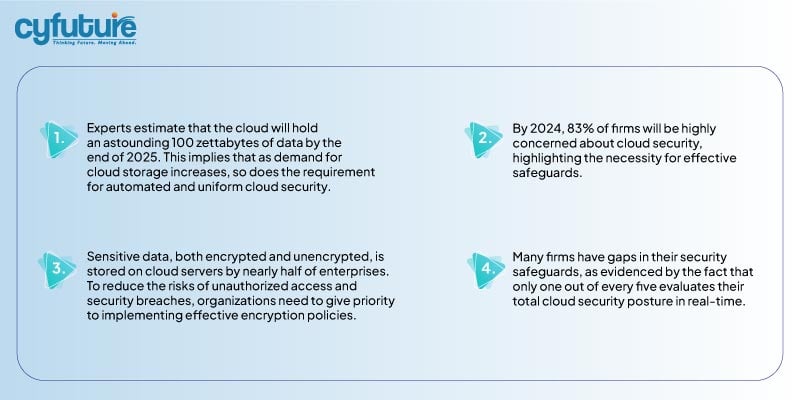
Now, let’s delve into the deep knowledge pool!
Cloud Security Services in India encompasses a comprehensive array of strategies and technologies in order to safeguard information and applications in cloud computing. Such includes data encryption, identity management, threat detection, to mention but a few, and incident response services amongst others, and they are used to boost defenses against an increasingly changing attack landscape.
A proper approach to cloud security assures that security is incorporated into every step of the cloud lifecycle, be it design, deployment, or continuous management. Implementing a robust cloud security framework is not only the best practice but one of the necessities to minimize the risks.
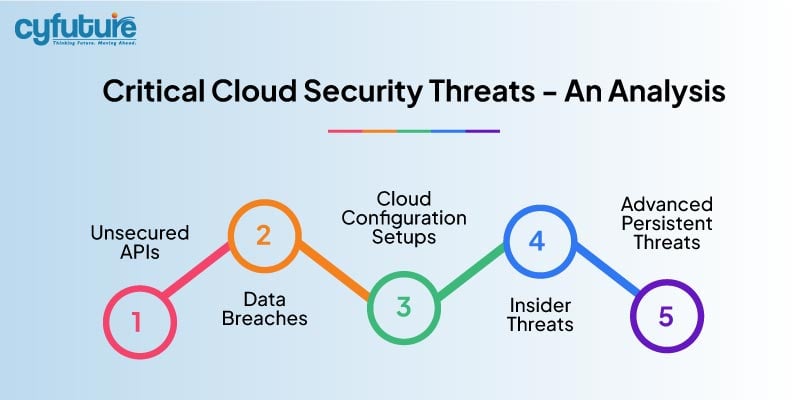
Arguably, the most dreaded cloud security threat is a data breach since it can bring havoc in reputation as well as in the organization’s financial standing. There can be access and exposure to sensitive data which can leak personal information, intellectual property, as well as trade secrets.
Insider threats, malicious or otherwise non-malicious, pose a grave threat to cloud security. Employees, contractors, or third-party vendors can gain access to critical systems and compromise data integrity and confidentiality.
Advanced Persistent Threat is a sophisticated, advanced, stealth cyber-attack that gains access and stays in the network for a protracted period, slowly exfiltrating data over time. Aside, advanced persistent threats often have highly skilled adversaries or nation-states as their enemies.
Application Programming Interfaces (APIs) are the backbone of cloud services, making cloud services interoperable and functional. However, flawed APIs can become weak points through which attackers can leverage a vulnerability to infiltrate sensitive data.
Misconfigured cloud settings form among the most common incident causes that should be reasonably avoided. Storage buckets, security groups, and access controls are the common items that can get misconfigured, inadvertently exposing sensitive data onto the public internet.
Navigating the labyrinthine intricacies of cloud security necessitates astute strategic consulting, which profoundly influences an organization’s defensive posture. Selecting consultants with acumen aligned to your organizational imperatives, nuanced requirements, and aspirational benchmarks ensures the provision of sagacious advice and pragmatic insights essential for fortifying your cloud security framework.
The journey commences with a meticulous risk assessment, encompassing vulnerability identification and threat modeling, subsequently advancing to rigorous compliance audits and the deployment of sophisticated security paradigms. Through this comprehensive consultancy, organizations are empowered to construct a resilient, impenetrable cloud architecture, encompassing robust encryption methodologies, seamless identity and access management, and cutting-edge intrusion detection systems.
This holistic approach guarantees not only compliance with stringent regulatory mandates but also the realization of an unassailable, fortified cloud environment that can adeptly withstand the evolving cyber threat landscape.
Using cloud computing services, one can enhance security using built-in features and scalable solutions. Major cloud providers have a huge number of tools and services that protect data and applications.
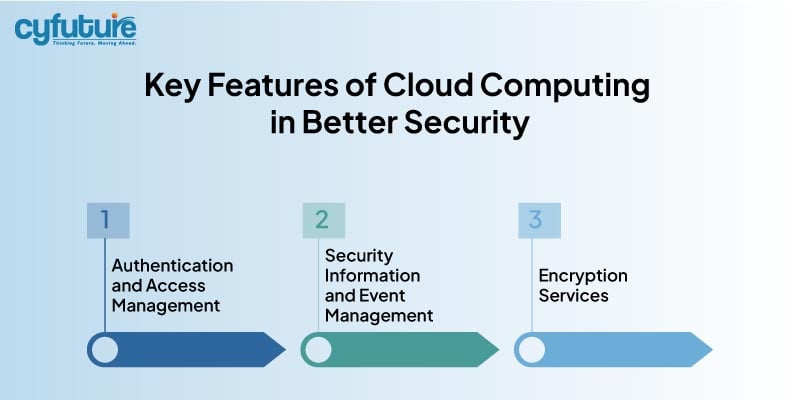
This feature would manage end-user identities in a centralized manner and streamline the process concerning access.
SIEM solutions aggregate and analyze security data to detect and respond to threats in real-time.
The managed encryption services ensure data is safe at all lifecycle stages.
In this view, cloud security is a constantly evolving and shifting landscape that calls for a strong proactive and vigilant stance. By acknowledging these serious threats outlined in the blog, organizations will come a long way in mitigating and strengthening their cloud environments, hence better protecting their digital assets.
These are the cloud security services in India, cloud strategy consulting, and cloud computing services that all come under the umbrella of resilient cloud security. Only through the firm lines of security, vigilance, and innovation will we manage to keep pace with what surrounds us while moving forward in this ever more complex digital era.
Join hands with Cyfuture to reach the future of secure cloud computing. An expert in navigating the intricate realm of cloud security, Cyfuture guarantees a comprehensive suite of cloud security services and expert consulting that empowers organizations to go above the bar of security challenges and deliver unparalleled success in their digital endeavors.
Data breaches, insider threats, advanced persistent threats (APTs), insecure APIs, and misconfigured cloud settings are among the most overlooked key cloud security threats. Each of these threats significantly jeopardizes the integrity, confidentiality, and availability of data stored in the cloud.
Insecure APIs may be used as an entry point by attackers that exploit these weaknesses and allow unauthorized access to sensitive information. API security is about routine security testing; proper authentication and authorization; monitoring API traffic constantly for abnormal patterns or behaviors that may signify malicious operations.
Misconfigured storage buckets and security groups inadvertently cause critical data exposed to some unregistered access. The tools that can be used in mitigating these risks are through automated configuration management tools, which are conducted periodically, and following the industry-standard compliance frameworks.
A proactive cloud security strategy includes identifying potential threats and is driven by strong security measures, such as encryption, MFA, and continuous monitoring. It involves regular security audits and staying abreast of emerging threats and best practices in dealing with them.
Changed is this very dynamic nature of cloud security threats. The only constant, as applied to security practice improvement, is change and thus becomes necessary for organizations to stay on guard and evolve in order to mitigate risks, protect sensitive information, and maintain integrity and availability in cloud services.